Experts outline 10 ways to secure older Macs as software support wanes
Owners of aging MacBooks, iMacs and Mac minis can reduce risk by enabling updates, tightening settings and protecting data even when major macOS upgrades are no longer available.
Owners of older Mac computers can significantly reduce their exposure to malware and other threats by following a set of practical security steps, security experts and Apple guidance show. Built‑in protections on Macs help, but machines that no longer receive full macOS upgrades require extra attention.
Many of the measures are simple changes to existing settings, while others involve installing updated apps, changing how the machine connects to networks and maintaining reliable backups. Users do not have to replace an aging Mac immediately to improve its security posture.
-
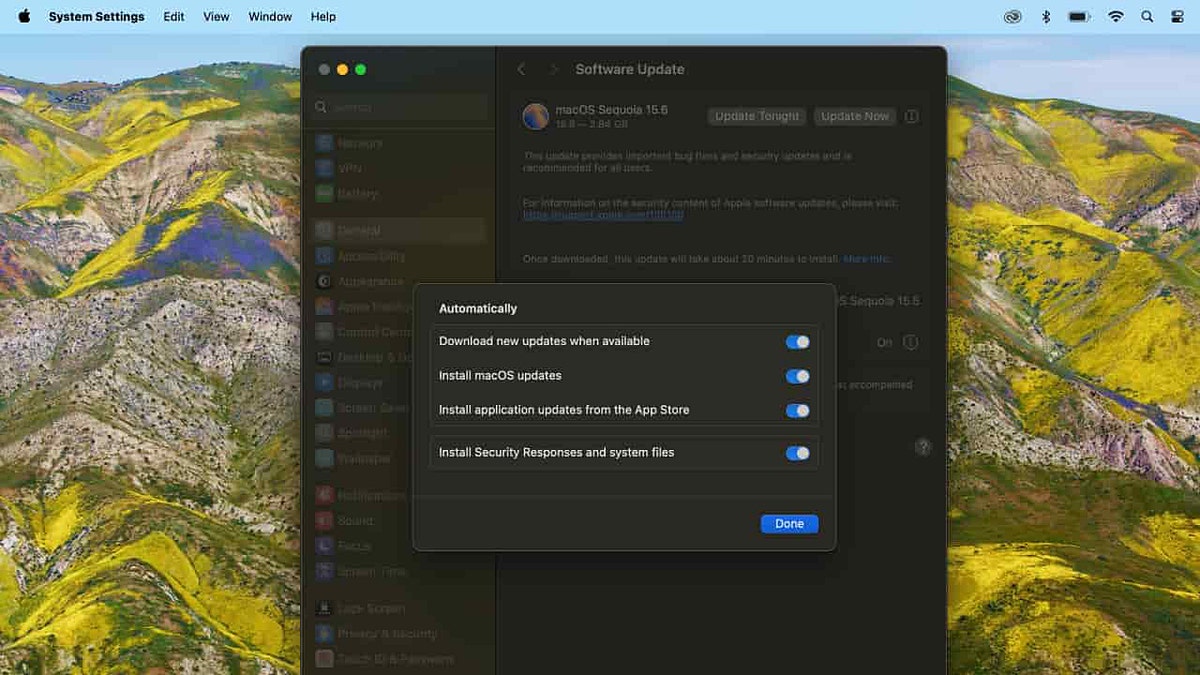
Keep the system as up to date as possible. Even when a Mac is no longer eligible for the latest macOS release, Apple sometimes issues security patches for older supported versions. Enable automatic updates by opening the Apple menu, choosing System Settings or System Preferences, selecting Software Update, and turning on automatic installation for updates and security patches. Regularly check for and install available updates for the operating system and built‑in apps.
-
Turn on the firewall and limit incoming connections. macOS includes an application firewall that blocks unsolicited inbound network traffic. Users should enable the firewall in System Settings or System Preferences under Security & Privacy and configure it to block incoming connections from apps that do not need them. Consider enabling stealth mode, which prevents the Mac from responding to unauthorized network probes.
-
Encrypt the drive with FileVault. Full‑disk encryption helps protect data if a device is lost or stolen. FileVault is available in Security & Privacy settings; when enabled it encrypts the Mac’s storage and requires the account password to unlock the drive on boot. Users should store their recovery key securely or associate it with their Apple ID where available.
-
Use a standard, non‑administrator account for day‑to‑day work. Running daily tasks from an administrator account increases risk because malware that gains control of that account may obtain elevated privileges. Create a separate standard user account for routine use and keep administrator credentials restricted to system changes and software installations.
-
Keep browsers and third‑party apps current or use alternatives that still receive security updates. Many attacks exploit outdated browsers, plugins and utilities. If the Mac’s native browser no longer receives updates on an older macOS, consider using a modern browser that still supports that version of the operating system, and ensure extensions are vetted and up to date.
-
Run reputable anti‑malware software and scan regularly. While macOS includes protections such as XProtect and Gatekeeper that block known malware and untrusted apps, additional anti‑malware tools from established vendors can provide detection and removal for newer threats. Keep any security software updated and run periodic scans.
-
Harden sharing and remote access settings. Disable services that are not needed, including Remote Login (SSH), Remote Management, File Sharing, AirDrop in public settings, and legacy services that expose ports to the network. Those options are found in Sharing preferences; turning off unneeded items reduces the attack surface.
-
Strengthen authentication: strong passwords, a password manager and two‑factor authentication. Use unique, complex passwords for device and account logins and store them in a reputable password manager. Enable two‑factor authentication for the Apple ID and other critical accounts to add a second layer of protection against credential theft.

-
Secure networks and use a virtual private network on untrusted Wi‑Fi. Avoid public or unsecured wireless networks when possible. When connecting in public, use a trusted VPN service to encrypt traffic and reduce the risk of eavesdropping. At home, ensure the router firmware is current and that the Wi‑Fi network uses strong encryption such as WPA3 or WPA2 with a strong passphrase.
-
Back up often and verify backups. Regular backups protect against ransomware, hardware failure and accidental deletion. Use Time Machine with an external drive or a networked backup destination, keep at least one recent offline or offsite copy, and periodically test restoring files to verify backup integrity.
Apple’s ecosystem includes several built‑in safeguards, including Gatekeeper, notarization checks for downloaded apps and XProtect signatures that block known malware, but security researchers have shown that sophisticated attackers can sometimes bypass those layers, particularly on older software. That makes the steps above important for users who want to extend the useful life of their machines without taking on unnecessary risk.
When a Mac is so old that it no longer receives any security patches, users face three options: accept a higher risk and isolate the device from sensitive data and networks, replace the hardware with a supported machine, or repurpose the device for offline tasks and regular backups. Enterprises and users with sensitive information should weigh replacement sooner rather than later.
Applying these practices can reduce the likelihood of compromise and slow attackers who rely on unpatched vulnerabilities. Regular maintenance, cautious browsing and disciplined backup routines remain the most effective defenses for older Macs that are no longer on the cutting edge of Apple’s software support.