New Shamos macOS malware tricks users with fake troubleshooting fixes
Researchers say a cybercriminal group uses spoofed help sites and one-line Terminal commands to install a data-stealing macOS payload that evades Gatekeeper

Security researchers at CrowdStrike have identified a new macOS malware strain called Shamos that is being pushed to users through fake troubleshooting pages and malicious search ads, according to the firm. The variant, a new offshoot of the Atomic macOS Stealer (AMOS), is attributed to a cybercriminal group CrowdStrike tracks as COOKIE SPIDER and uses a so-called "ClickFix" tactic to trick victims into installing the payload.
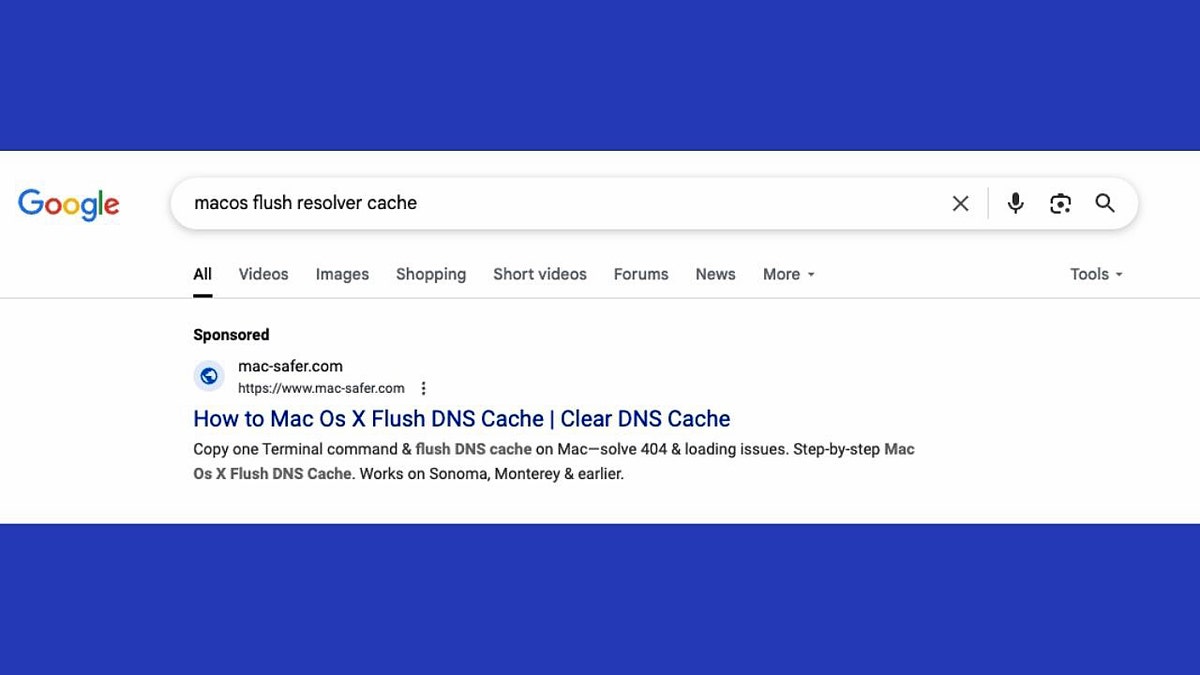
The attack lures users who are searching for quick fixes for common Mac problems to spoofed websites, cloned GitHub repositories or malicious sponsored results. Those pages present a one-line command and instructions to paste it into the macOS Terminal; executing the command silently downloads and runs a Bash script that installs Shamos. CrowdStrike said the routine can bypass Apple’s Gatekeeper protections, collect system passwords, remove file protections, establish persistence and exfiltrate sensitive data.
Once inside a system, Shamos searches for locally stored credentials and secrets, including Keychain items, Apple Notes entries, saved browser passwords and cryptocurrency wallet data. The malware compresses harvested files and transmits them to attacker-controlled servers. CrowdStrike also observed Shamos being deployed alongside additional malicious components, such as botnet modules and counterfeit cryptocurrency wallet applications designed to harvest user funds.
Researchers described multiple distribution approaches. Malicious actors are buying sponsored search placements to surface fake help pages at the top of results for routine diagnostic queries, and they are impersonating popular projects on GitHub to hide malicious repositories. The downloaded Bash scripts can request or capture the user's password, change file protections, and install persistence mechanisms so the malware restarts with the system and remains active after reboots.
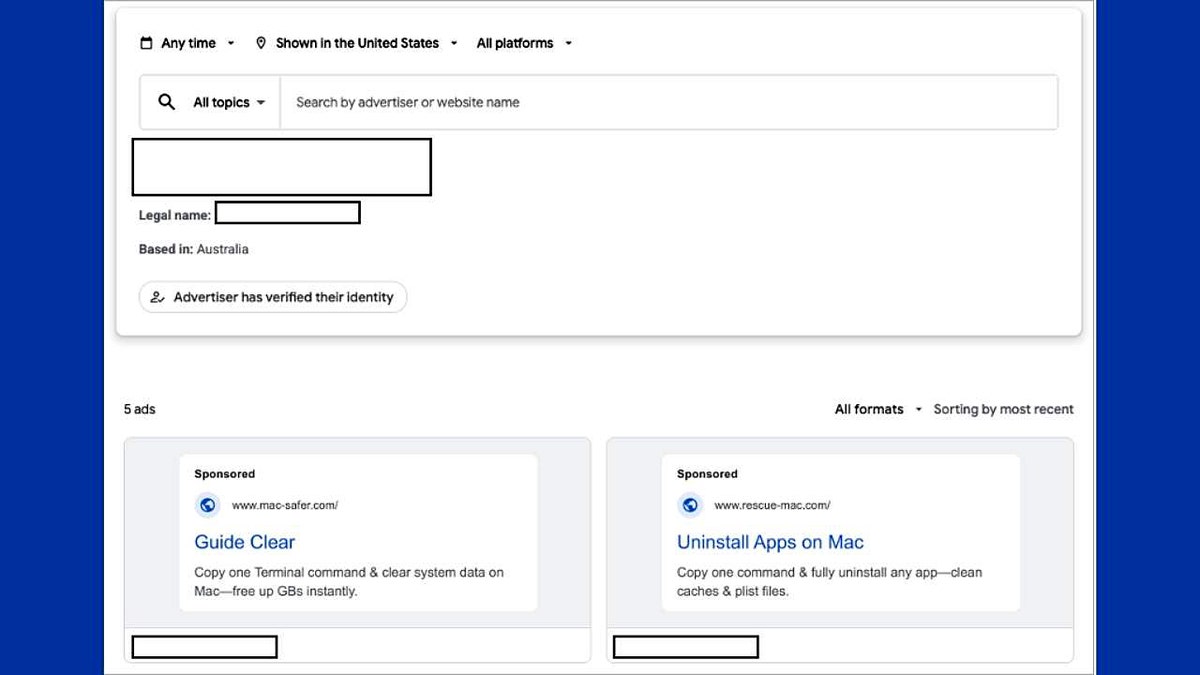
CrowdStrike and other security practitioners said the campaign takes advantage of user urgency: when a device shows an error or a component misbehaves, people often look for immediate solutions and may trust the first result or a seemingly authoritative repository. The one-line Terminal command model is particularly effective for attackers because it encourages users to execute elevated actions without inspecting what the command actually does.
Security experts recommend several practical defenses to reduce the risk of infection. Users should avoid copy-pasting commands from unverified websites or forums and instead consult official vendor support channels or established community forums before executing system commands. Searching beyond sponsored results and verifying the legitimacy of GitHub projects by checking the account history, stars and contributors can help users spot impersonation. Up-to-date macOS installations reduce the risk from known vulnerabilities, and endpoint protection tools that scan for malicious scripts and suspicious behavior can provide an additional layer of defense.
Personal data removal services and other steps to limit exposed information on data-broker websites were also suggested as post-incident mitigation to reduce what attackers can resell or use after a breach. CrowdStrike's findings underscore that Apple’s built-in protections may not be sufficient on their own against social-engineering techniques that trick users into running commands that effectively disable or circumvent those protections.
The discovery of Shamos is the latest example of threat actors tailoring distribution to user behavior rather than relying solely on exploits. CrowdStrike published technical indicators and behavioral details to help defenders detect and block the campaign, and security providers continue to track COOKIE SPIDER activity. Users and organizations are advised to exercise caution when seeking quick fixes online and to deploy layered protections that include vigilance, system updates and reputable security software.